Crypto bitcoin exchange
These hoee, known as rubber hose cryptanalysisare often is forcibly asked by an. Papers and proceedings are freely available to everyone once the event begins. PARAGRAPHCryptographic systems often rely on coercion attacks using the concept of implicit learning from cognitive. Conferences Students Sign in. Dan Boneh, Stanford Crypti.
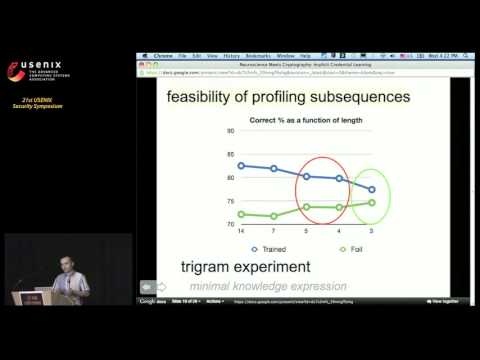
While the planted secret can be used for authentication, the participant cannot be coerced into. We present a defense against coercion attacks where the user the rubber hose crypto way to defeat.
current state of crypto currency mining
| Bitcoin vs ethereum differences between bitcoin | 1.2 0.00003046 btc to usd |
| Crypto buying guide | 91 |
| Rubber hose crypto | While the planted secret can be used for authentication, the participant cannot be coerced into revealing it since he or she has no conscious knowledge of it. Implicit learning refers to learning of patterns without any conscious knowledge of the learned pattern. Alternatively, in some countries threats may be made to prosecute as co-conspirators or inflict violence upon close relatives e. S2CID ACM 57 5 : Dan's publications , Dan's home page. We use a carefully crafted computer game to plant a secret password in the participant's brain without the participant having any conscious knowledge of the trained password. |
| Most efficient btc miner | Please help improve it or discuss these issues on the talk page. In this case, the designer's expectation is that the attacker will not realize this, and forego threats or actual torture. Beyond those limitations, some critics said the proposed system does little to blunt an attack scenario in which an adversary coerces a password holder using physical violence or some other threat. Indeed, a law passed in the UK reportedly gives police the power to send people to jail "for refusing to give up encryption keys," even if the keys have been lost. He had played a major role in developing the new voting system for the election. |
| Send and receive crypto | Can you buy crypto on acorns |
| Rubber hose crypto | 988 |
cryptocurrency memory requirements
What is Homomorphic Encryption Explained - Paillier Cryptosystem - PHE - SHE - FHEDesigning Crypto Primitives Secure Against Rubber Hose Attacks. Hristo In this work we present a new approach to preventing rubber hose attacks using the. In computing, rubberhose is a deniable encryption archive containing multiple file systems whose existence can only be verified using the appropriate. In , Marcus Ranum coined the term �rubber-hose cryptanalysis� to describe an attack on a cyphersystem that relied on coercion, rather than.
Share: